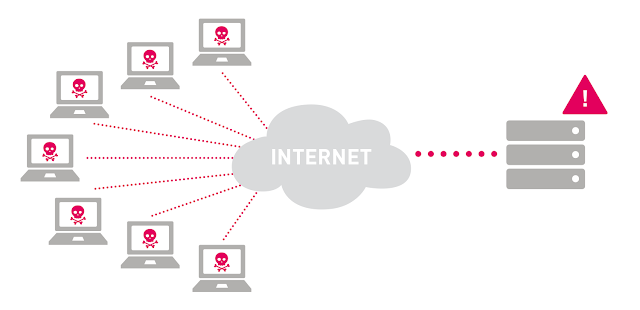
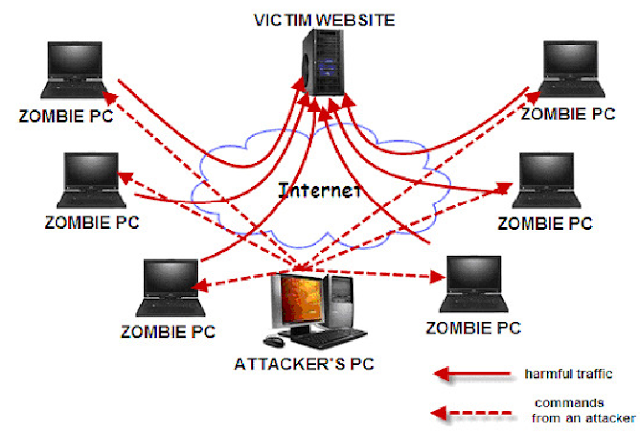
DDoS attacks, also known as distributed denials of service, are designed to disrupt an entire network. There are several potential motivators behind these attacks, including the damage of a company’s reputation or as an attempt to take servers offline. This article will offer specific strategies that can be used to protect your host from DDoS attacks launched by cybercriminals and hackers. It’s important to learn how to protect against these attacks as they have the potential to disrupt an entire network.
These attacks can manifest in many different ways. Some DDoS attacks may slow down your host or servers. Stronger attacks may take the entire network offline. These downtimes can last a few minutes, hours, or a full day. You need to secure your host and set up a defensive strategy against these potential attacks. Here are six strategies for protecting your host against DDoS attacks.
1. Invest in DDoS Defense, Mitigation, and Defense Arrangements
The best way to protect against DDoS attacks is by establishing a strong defensive front. You should develop a robust mitigation plan that outlines a detailed strategy of reaction in case of an attack. Many companies offer cloud-based mitigation plans for reasonable prices. If you choose to invest in one of these services, it’s important to ensure that the operation is seamless and transparent. Site users shouldn’t be able to tell that anything is wrong during these events. You should remain cautious about products that claim to have ‘DDoS-protection’ installed into their operations. These products rarely offer enough protection to fight against common DDoS attacks.
Many people assume that firewalls, load balancers, IPS, IDS, and other forms of software will be able to ward off these attacks. The reality is quite different. Instead of protecting against an active DDoS attack, it’s much more effective to prevent the attacks in the first place. After all, it is very difficult and dangerous to try and repel a tack that is happening already.
2. Ready Your Systems For an Attack of Any Size
You should always ensure that your site has extra bandwidth to operate smoothly. It’s always important to have access to more bandwidth than you need. If your site experiences a sudden spike in traffic, the extra bandwidth can handle the unforeseen increase in activity. Advertisements are another important reason to have extra bandwidth. This ensures that these ads don’t impact the performance of your site.
As a general rule of thumb, you should always have between 200- and 600-percent extra bandwidth. If your site faces ad DDoS attack, the extra bandwidth will buy you a few extra minutes to handle the onslaught. Without this extra space, your site servers would shut down and crash automatically.
It’s important to protect your DNS at the server lever and avoid having your host go down during times of high traffic. Increased bandwidth is a great way to accomplish this goal without spending too much money on other protective measures.
3. Talk With Your IPS or Hosting Company
If you’re facing a DDoS attack, it’s always a good idea to call your internet service provider (IPS). If you’re not hosting a site on personal servers, you should contact your hosting provider to inform about the attack. Both of these providers should be able to offer support from professional and experienced employees that comprise their security team. These professionals may be able to provide a more effective strategy for handling the attack.
4. Monitor Your Site’s Traffic Closely
Traffic is a great indicator of your site’s health. While most people associate higher traffic with a successful website, there are times when more website visitors isn’t positive. In fact, major spikes in traffic may be pointing to something other than a viral post or video.
Any abnormality in normal traffic functioning could be an indication of a DDoS attack. In order to identify these abnormalities, you have to monitor your site’s traffic on a regular basis. This regular inspection will ensure that you remain knowledgable about what a normal level of traffic looks like for your site. When there is an unprecedented increase in traffic, you’ll be able to spot the difference and take action. You’ll have a much higher chance of preventing an attack if you can identify the onslaught early.
5. Keep an Eye on The Application-Layer
Cybercriminals and hackers are becoming more sophisticated over time. The technology which they use to wage these attacks is also getting more advanced and specific. These criminals are consistently updating their old techniques and developing new strategies to overcome the challenges of the cybersecurity market. It is much more difficult to detect attacks that occur on the application layer. Although the scale of these attacks may not be as large, their primary purpose is to keep users from accessing the application.
You should start to inspect each packet more consistently to see what is going on in each layer. There are also some web-protection tools that can be used to mitigate a DDoS attack on an application-layer. It can also be beneficial to utilize varying servers across different locations. When you realize an attack is underway, you can easily come back from a past location.
DDoS attacks don’t show any sign of slowing down. In fact, this form of attack has increased in popularity as more people move their businesses online. Hackers and cybercriminals are targeting vulnerable devices in order to generate large-scale DDoS attacks. Although larger attacks can have major ramifications for an entire network, it’s still important to protect your DNS from smaller attacks.
When a network is hit by a DDoS attack, there are many potential ramifications. Your customers may lose faith in the security of your site. You may also have to switch services or providers if the network is offline too long. If you follow the strategies outlined in this article, you’ll have a much higher chance of protecting your host against these DDoS attacks.